First let me introduce myself, my name is Derk van der Woude. I’m a principal Consultant at InSpark (Microsoft country partner of the year 2018). In my role I’m responsible for Security & Compliance:
- Member of the Technology Board
- Owner of the Security and Compliance Expert team
- Product owner (technical) of the Cloud Security Center (SOC as a Service)
If you want to connect, please visit my LinkedIn page. This blog describes the Microsoft Identity Security solutions powered by the Cloud for SecAdmins (Protect) and SecOps (Detect & Respond).
Identify
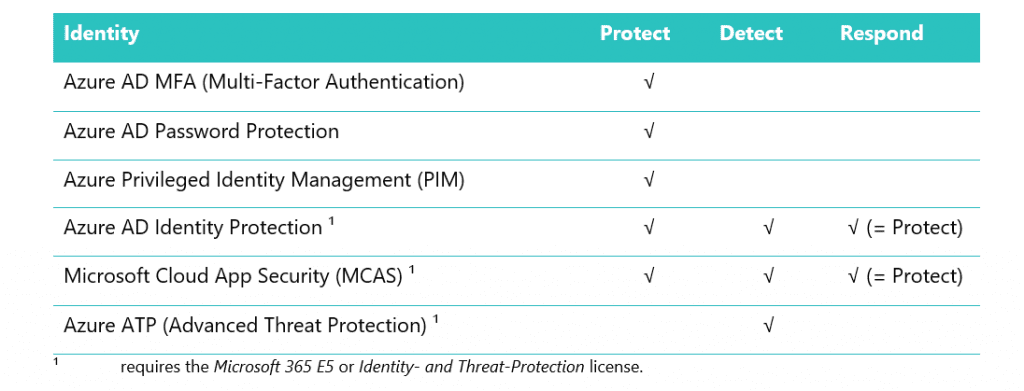
The NIST Cybersecurity Framework consists of five functions¹:
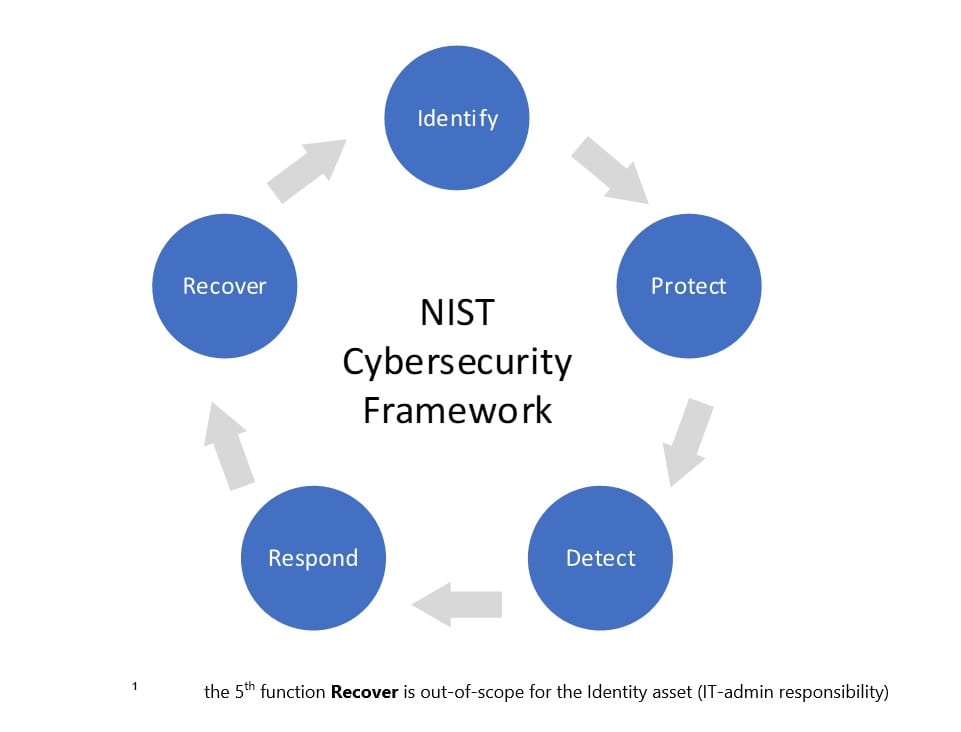
The 1th function of the NIST Cybersecurity framework is Identify This function identifies the company assets to protect from a business perspective. The asset to protect in this blog is the Identity from a user perspective (can also be used from an admin perspective) on the ‘modern’ workplace¹.
¹ The Modern Workplace in the Microsoft definition consists of Windows 10 Enterprise (the only Microsoft client operating system developed for working safely in an Online world) and SaaS applications like Office 365 for the Microsoft productivity suite. The four components in the framework (below) can be used for any type of workplace (computer, mobile, on-premises, cloud, etc.).
The ‘modern’ workplace¹ framework which consists of four components:
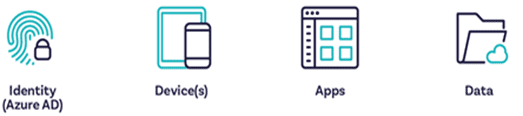
A user (identity) a has one or more device(s) (computer and/or mobile) to open an application (e.g. Outlook) to access data (e.g. e-mail). Protection requires a defense in-depth approach; each component is vulnerable for attacks and/or data-leakages.
The asset to protect in this blog is the Microsoft Identity stored in the Azure AD and/or on-premises AD (Active Directory).
Protect
The 2nd function of the NIST Cybersecurity framework is Protect. Protect is a SecAdmin (Security Administrator) responsibility who implements Security solutions to comply (mitigate risks) with the Security Policy (CISO – Chief Information Security Officer – responsibility).
The Identity is the New Perimeter in an Online world (Modern Security). The traditional approach of protecting the Identity is using (forcing) complex passwords which need to be changed every 90 days (or another interval). This is not extra secure, nor user friendly. Why? Complex passwords are written down and required changes results in using tracking numbers (01, 02, 03, etc.).
Azure AD Password protection
A more secure and user-friendly Security solution which uses a unique (personal and easy to remember for end user) password instead of a complex password, is Azure AD Password Protection. Microsoft Azure AD is targeted 1.5 million times each day, all those attack passwords are stored in the ‘weak password’ database (other Security resources are used as well like the dark web), if a user wants to use (or change) a password, it’s verified against the data in the ‘weak password’ database. If there’s a match (all characters are also converted to lower case for more coverage on weak passwords), the user needs to use another unique password. The result is longer and unique password, but easy to remember because it’s personal to the user.
This still leaves us with the problem of changing the password every 90 days which is solved in the next parts; Azure MFA and Azure AD Identity Protection.
Azure MFA
Azure MFA (Multi-Factor Authentication) is the Microsoft solution for a second authentication factor because passwords are the weakest form of protection (shared between people and easy to steal via phishing for example).
Azure MFA uses two methods for authentication; something you know (password) and something you have (token on the mobile phone via the Microsoft Authenticator for example).
By using Multi-Factor Authentication, the requirement (from the Security policy) to change the password every 90 days is not needed anymore to secure the Identity. If a password is compromised, it cannot be used due to the second authentication factor.
Azure AD Privileged Identity Management (PIM)
Azure AD Privileged Identity Management (PIM) is a Security solution to comply with the Security principle of least privileges (part of every Security Policy). Azure AD PIM provides just-in time access for privileged (e.g. Global Administrator) accounts in Azure AD. Access is granted after verification via Multi-Factor Authentication and optional (advise: require for Global Administrator) approval from a manager (four eyes principle), always configure two approvers to avoid lock-outs.
Detect and Respond
The 3rd and 4th function of the NIST Cybersecurity framework are Detect and Respond. Detect and Respond is a SecOps (Security Operations) responsibility. If the Identity is protected by SecAdmins, it should be monitored 24×7 by SecOps in the SOC (Security Operations Center) and not by IT-admins due to conflicts of interest and separation of duties (basic Security principles from the Security Policy).
Almost every organization has an IT-department running from Monday till Friday, from 9AM – 5PM. Security (Identity- and Threat-Protection) is a 24×7 responsibility with a different mind- and skillset compared to regular IT.
I’ve seen IT-admins do ‘bad’ stuff and remove their traces (they have permissions to delete logs for example). Also ‘some’ IT-Admins use their privileged account (e.g. Domain Admin or synced Global Administrator) to retrieve e-mail and surf the web. One thing is certain, if that account receives malware you don’t have to worry about which files are encrypted (all files ☹).
There are three Microsoft Security solutions for Identity monitoring, monitoring are the functions Detect (Investigate) and Respond in the NIST Cybersecurity framework. Detect and Respond combined with automatic functions can be seen as Protect functionality.
The Microsoft Identity SecOps solutions are:
- Azure AD Identity Protection
- Azure ATP
- Microsoft Cloud App Security (MCAS)
Azure AD Identity Protection
The Azure AD Identity protection Detects and Respond to Security alerts on the Cloud identity (Azure AD). Azure AD Identity Protection solves the problem of the required password change, you should change the password when there is a valid reason: if the account is compromised (someone else has the password).
Azure AD Identity protection has two risk-based policies:
- Sign-in risk is a real-time detection function, also called risk-based multi-factor authentication. An example is impossible travel (a user logs on from the Netherlands and China within one hour, while the travel distance is ten hours) which results in an extra Multi-Factor Authentication challenge.
- User risk is an off-line detection function and requires a password change if a Security alert is detected. An example is leaked credentials (requires Azure AD password hash sync); when compromised credentials (username and password hash) are detected, (sold) on the dark web for example, and they match the Azure AD credentials, a forced password change is triggered to protect the Identity.
Many people use their business e-mail address for different SaaS solutions (e.g. Facebook, LinkedIn or Salesforce) and re-use their password, so if one service is compromised (e.g. LinkedIn in 2012) all other services are also ‘compromised’.
Azure ATP
Azure ATP (Advanced Threat Protection) detects anomalies in the on-premises Active Directory.
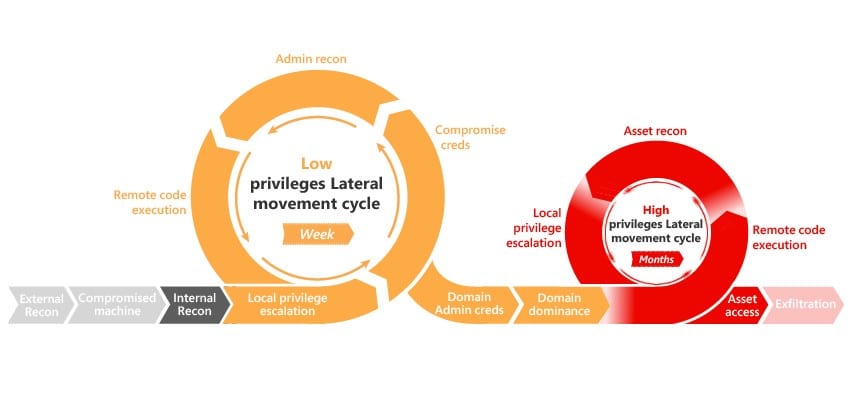
Detection is in each phase of the kill chain (reconnaissance, lateral movement, privilege escalation and domain dominance).
Azure ATP is the Cloud version of Microsoft ATA (Advanced Threat Analytics) with advanced functions compared to Microsoft ATA (e.g. multi-forest support) and Azure ATP is updated weekly instead of yearly with Microsoft ATA. Another advantage of Azure ATP is the integration with other Security solutions like Windows Defender ATP and MCAS (Microsoft Cloud App Security).
Microsoft Cloud App Security
The Microsoft Cloud App Security (MCAS) is the Cloud Access Security Broker (CASB) solution from Microsoft. Microsoft Cloud App Security protects the Identity but also Apps and Data. Identity protection is logon- and session-based. It detects anomalies during logon, e.g. non-Microsoft brute-force attack on Salesforce), and session-based anomalies, e.g. mass download if someone uploads a lot of data out of the tenant (this happens often if someone leaves the company) of e-mail forwarding (this also happens when someone leaves the company but we’ve seen malware also using the method for data exfiltration).
Microsoft Unified Identity Investigation
From a SecOps perspective we’ve seen three Security solutions which play an important role in the Identity Detection and Respond phases. It can be challenging to have a clear overview of all information.
A solution is coming, announced at Ignite 2018; Microsoft is working towards a Unified Identity investigation interface which integrates all three Identity Security solutions, described in the SecOps part of this blog, in one single view (the Microsoft Cloud App Security portal will be the single view) to get insights on the identity information correlated from all Security platforms.
For more information, you can read more about Unified SecOps Investigation for Hybrid Environments.
New Microsoft 365 Security and Compliance Offering
The SecOps tooling requires the Microsoft 365 E5 license for all users to be compliant, this can be expensive if only the Identity- and Threat Protection solutions are used. Part of the Microsoft 365 E5 license are also Compliance solutions like Advanced Data Governance or Azure Information Protection with automatic labeling, and advanced voice (PSTN) capabilities from the Cloud.
Identity & Threat Protection is the new license offering from Microsoft specially for SecOps protecting the Modern Workplace components. See this blog for more details.


